What is Infrastructure as Code (IaC)?
Infrastructure as code (IaC) leverages machine-readable configuration files to define and provision computing resources. Instead of manually configuring servers, networks, and other infrastructure components, you can define them in code, enabling automation, consistency, and scalability in modern cloud-native and DevOps environments.
By adopting IaC, we can significantly improve deployment speed, reduce the risk of human error, and ensure that infrastructure resources are reproducible and maintainable over time. As the complexity of systems grows, IaC provides the tools necessary to manage these environments efficiently.
This blog post explores the principles of infrastructure as code and popular tools that implement it. We’ll also discuss how Quali’s solutions enhance IaC practices and address common challenges to improve your infrastructure management processes.
Fundamentals of Infrastructure as Code
Understanding the core principles of IaC tools is crucial for leveraging their full potential. Let’s explore the fundamental elements that make IaC a transformative approach to infrastructure management.
Configuration files
At the heart of IaC are configuration files—text files that define infrastructure configuration settings. These files make it easy to version, reuse, and share setups across teams and environments. By storing configurations as code, we can track changes over time, collaborate using version control systems like Git, and ensure that our infrastructure setups are consistent and repeatable.
Declarative syntax
One of the fundamental principles of IaC is its adoption of declarative syntax, allowing us to define the desired end state of our infrastructure without specifying the exact steps to achieve it. The declarative approach enhances readability and simplifies maintenance.
Version control
Using version control systems is a best practice in IaC. Managing configuration file changes with tools like Git lets us enhance collaboration and auditing. By utilizing version control systems, DevOps and IT teams can collaboratively develop and manage infrastructure code, thoroughly review modifications, and effortlessly revert to earlier configurations when necessary.
Immutable infrastructure
Immutable infrastructure involves replacing infrastructure components rather than modifying them. When changes are needed, we deploy new instances with updated configurations and decommission the old ones. This practice reduces configuration drift and ensures consistency across environments.
Orchestration and automation
Automation is at the core of IaC. By automating the deployment and scaling of infrastructure components through code, we reduce manual effort and speed up deployment time.
Orchestration tools manage and sequence automated tasks, guaranteeing the proper order of resource provisioning, as well as precise configurations.
Idempotency
By embracing idempotency, we ensure that applying the same configuration repeatedly leads to a consistent infrastructure state without any unintended side effects. This property is essential for stabilizing infrastructure setups.
Modules and reusable components
Using modules and reusable components allows us to standardize configurations and promote infrastructure as code best practices across teams. Modules are pre-defined templates that encapsulate common infrastructure patterns, making setups more efficient and reducing the likelihood of errors.
Policy as code
Policy as code involves embedding compliance and security policies within our IaC configurations. Defining policies in code allows us to automatically ensure that all infrastructure adheres to internal standards and regulatory requirements.
State management
State management is about tracking the actual state of our infrastructure resources to guarantee they match the desired configurations. IaC tools maintain a state file or leverage state management services to record the current state. They can then detect changes, manage dependencies, and apply only the necessary updates to reach the desired state.
Key Infrastructure as Code tools
The landscape of infrastructure-as-code tools is continuously evolving, and each new tool has its own unique features and capabilities. We explore five popular solutions below.
Terraform
Terraform, developed by HashiCorp and released in 2014, has quickly become a leading tool in the IaC space. It is a versatile choice for teams adopting multi-cloud strategies, as it can handle infrastructure across cloud providers and on-premises data centers.
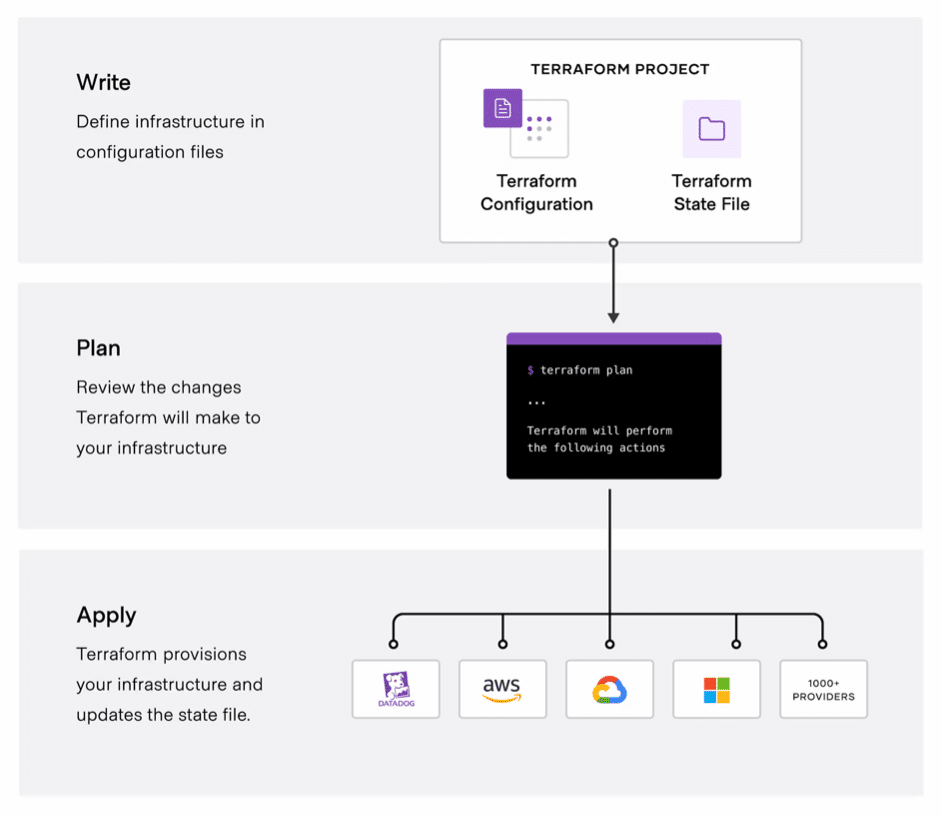
Figure 1: Terraform overview (Source: HashiCorp)
Advantages
- Multi-cloud support: Lets you simultaneously manage cloud resources across multiple providers
- Declarative syntax: Implements HashiCorp Configuration Language (HCL), which is both human-readable and machine-parsable
- Strong community and ecosystem: A robust ecosystem of modules and active community contributions significantly expand its functionality
- Infrastructure graphing: Builds a dependency graph for efficient planning and execution
Disadvantages
- State management complexity: Requires careful handling of state files to avoid conflicts, especially in team environments
- Learning curve: Poses a challenge for newcomers, who may need time to master its syntax and concepts
- Limited native testing: Lacks built-in testing frameworks, instead relying on third-party tools
State management and best practices in Terraform
Terraform uses a state file (terraform.tfstate) to keep an updated record of the infrastructure resources it manages. This state file is crucial for operations like “plan” and “apply” since it records the mapping between resources defined in your configuration and those deployed in the real world.
The following are recommended practices:
- Remote state storage: Save the state files in centralized external systems like AWS S3 to enable team collaboration.
- State locking: Implement state locking so that only one operation can make changes to the state at any given time, avoiding conflicts and state corruption.
- Sensitive data handling: If your state files contain confidential information, be sure to encrypt them to safeguard against unauthorized access.
OpenTofu
OpenTofu has emerged as a community-driven, open-source initiative that introduces a new way to manage infrastructure using code. It aims to provide an open, vendor-neutral solution for infrastructure provisioning, fostering transparency and collaboration.
Advantages
- Vendor-neutral design: Designed to avoid vendor lock-in and promote openness
- Community-driven development: Encourages contributions and transparency
- Extensibility: Built to be adaptable to various use cases and platforms
Disadvantages
- Early development stage: May lack features and stability compared to more mature tools
- Smaller ecosystem: Fewer modules and community resources available
- Limited support: Limited enterprise support and documentation
Custom providers in OpenTofu
OpenTofu allows developers to create custom providers to support various platforms with more freedom. This extensibility is achieved through a plugin architecture, where providers can be developed in languages like Go.
AWS CloudFormation
Since its launch in 2011 by Amazon, AWS CloudFormation has provided a native infrastructure-as-code platform, enabling us to define and deploy AWS resources using declarative templates. It empowers developers and system administrators to model, provision, and manage AWS infrastructure deployments in a predictable and repeatable manner.
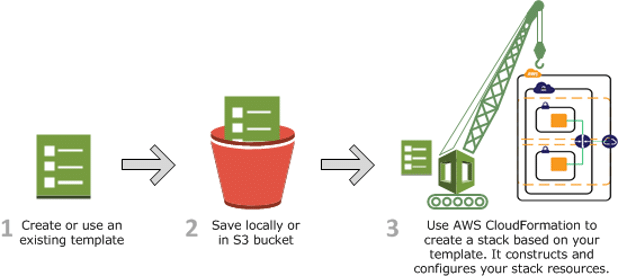
Figure 2: AWS CloudFormation overview (Source: AWS Docs)
Advantages
- Deep AWS integration: Full support for AWS services and features
- No additional cost: Free to use; pay only for the AWS resources created
- Change sets: Allows previewing changes before applying them
- Drift detection: Identifies resources that have drifted from the stack’s template
Disadvantages
- AWS-specific design: Limited to AWS; not suitable for multi-cloud strategies
- Template complexity: Templates in JSON or YAML, which can become complex and verbose
- Feature lag: Potentially delayed availability of new AWS services
Stack management and best practices in CloudFormation
By grouping AWS resources into stacks, CloudFormation allows you to manage them collectively as a single, cohesive unit. By using nested stacks, you can reuse templates and organize resources logically.
The following are recommended practices:
- Modular templates: Create smaller, reusable templates out of larger ones.
- Parameterization: By incorporating parameters into your templates, you can tailor them for different environments, enhancing flexibility and reusability.
- Change sets: Review changes before applying them to avoid unintended disruptions.
For a comprehensive comparison of Terraform and AWS CloudFormation, check out our blog post.
Ansible
Ansible, created in 2012 and purchased by Red Hat in 2015, started as a configuration management tool but has expanded to include IaC capabilities. Ansible sets itself apart with its straightforward approach and agentless architecture, allowing us to manage and automate infrastructure without the need to install additional software on target systems.
Advantages
- Agentless architecture: By utilizing SSH for communication, Ansible manages systems without the need to install any agents on the target nodes
- Simple YAML syntax: Uses human-readable YAML files for playbooks
- Versatility: Manages both infrastructure and software configurations
- Large module library: Features extensive modules for managing various systems and services
Disadvantages
- Imperative approach: Is more procedural than declarative, requiring detailed instructions
- Scalability limitations: May face challenges in very large environments
- No state management: Lacks built-in state management for tracking resource states
Inventory management and best practices in Ansible
Groups of hosts are defined by Ansible via an inventory file. By leveraging dynamic inventory scripts, it can automatically query cloud providers to discover hosts and gather their configuration details.
The following are recommended practices:
- Dynamic inventory: Automatically manage hosts in cloud environments using dynamic inventory.
- Playbooks: Use roles and include statements for reusability when organizing playbooks.
- Idempotent tasks: Design your tasks to be idempotent, allowing them to run repeatedly without causing unintended changes or errors.
Helm
Helm is often called the “package manager for Kubernetes” and is a part of the Cloud Native Computing Foundation (CNCF). Developers use it for easier application deployment and management in Kubernetes.
Advantages
- Simplified Kubernetes deployments: Packages applications into charts for easy management
- Reusable charts: Enables the sharing and reuse of application configurations, allowing teams to consistently deploy applications
- Versioning and rollbacks: Allows for easy release upgrades and rollbacks
- Templating engine: Uses Go templates for dynamic infrastructure as code definitions
Disadvantages
- Kubernetes-specific design: Only applicable within Kubernetes environments
- Template complexity: Can become intricate for complex applications
- Overhead for simple deployments: May be excessive for straightforward applications
Chart dependencies and best practices in Helm
Helm allows charts to depend on other charts, enabling complex applications to be managed effectively.
The following are recommended practices:
- Version control charts: Keep your charts in a repository for collaboration.
- Helm repositories: Store and share charts using repositories.
- Secrets management: Use tools like helm-secrets to carefully handle sensitive data.
Challenges in implementing IaC
While IaC offers significant advantages, there are challenges when implementing it at scale.
Security and access control
Protecting sensitive information and ensuring that only authorized personnel can modify infrastructure code are crucial for maintaining security in infrastructure management.
Challenges include:
- Secret management: Ensuring that API keys and passwords are handled securely to prevent unauthorized access and data breaches
- Access policies: Managing and enforcing role-based access control (RBAC) for restricting permissions according to specific roles and responsibilities
- Audit trails: Maintaining comprehensive records of who changed what and when to support accountability and compliance
Complex orchestration needs
Handling complex, multi-cloud, and hybrid environments requires advanced orchestration capabilities. DevOps teams need tools to manage dependencies, coordinate resources across a variety of platforms, and maintain a unified view of their entire infrastructure.
Challenges include:
- Interdependencies: Managing relationships between services
- Diverse environments: Consistency across different cloud providers
- Scalability: Orchestrating large numbers of resources
Governance and compliance at scale
As teams grow, maintaining visibility, enforcing policies, and controlling costs become more challenging. They need solutions that provide oversight and automation to ensure the infrastructure setup adheres to regulatory requirements and upholds internal standards.
Challenges include:
- Policy enforcement complexity: Implementing consistent policies across diverse teams and environments
- Compliance monitoring: Continuously tracking compliance with regulations like GDPR, HIPAA, etc.
- Visibility: Achieving a complete overview of all deployed resources and actively monitoring their compliance status
For more insights on how IaC solutions can benefit your DevOps teams, read our blog “Why Infrastructure as Code Alone Doesn’t Work for Enterprise DevOps.”
Quali’s Infrastructure as Code solutions
Quali offers cutting-edge solutions to enhance and simplify infrastructure-as-code (IaC) practices. It provides robust tools for provisioning, governance, and visibility, helping teams overcome common challenges associated with IaC at scale.
Quali Torque
Quali Torque transforms the complexity of IaC into a streamlined, user-friendly process. Its self-service infrastructure provisioning platform secures sensitive cloud credentials, automates compliance, and enables rapid delivery of environments across the application lifecycle.
Automated IaC creation via cloud resources
Torque connects to the user’s cloud accounts, discovers resources deployed via those accounts, and enables the user to automatically create and download open-source Terraform and OpenTofu files defining the state of those resources. This accelerates the creation of assets that can be used via the user’s repositories and/or deployed and managed via Torque.
Simplified IaC provisioning
Torque allows DevOps teams to set up self-service IaC provisioning workflows, enabling them to deploy infrastructure without requiring deep technical knowledge or access to cloud credentials.
By abstracting parameters and simplifying configurations, Torque empowers developers to quickly access the resources they need while maintaining operational control.
Environment orchestration with AI
Torque leverages AI to orchestrate blueprints for environments, such as development, testing, or production, using IaC modules. This feature accelerates the deployment and reuse of pre-defined environments, ensuring consistency and efficiency. Users can design complex infrastructure templates and manage dependencies seamlessly.
Automated Day-2 Operations
Since Torque initiates the provisioning and monitors the operation of infrastructure defined in IaC, the platform can execute actions on that infrastructure automatically.
Torque defines Day-2 actions as scripts and enables users to execute them via a single click in the Torque UI, while also providing the option to automate these actions based on custom triggers, including recurring schedules and in response to events.
Governance and compliance
Governance is a cornerstone of Torque, with the platform discovering and enforcing policies based on the user’s policy files to prevent non-compliant infrastructure deployments. Whether for security, regulatory compliance, or cost control, Torque ensures every resource provisioned adheres to standards in place. This proactive approach minimizes risk by denying requests that violate established policies.
Reporting and cost visibility
Torque provides detailed reporting on resource usage, associated costs, and user activity. This transparency enables teams to monitor cloud expenses, track provisioning patterns, and hold users accountable for their infrastructure actions. Such insights facilitate collaboration and identify areas for cost optimization.
Integration with popular tools
Torque integrates seamlessly with leading DevOps and platform engineering tools like Terraform, Ansible, Kubernetes, and CI/CD pipelines. This interoperability makes it easier to adopt Torque in existing workflows, maximizing its value for DevOps and IT teams already invested in IaC practices.
Cloud Curate
Cloud Curate bridges the gap between unmanaged cloud infrastructure and codified IaC practices. It lets teams discover, document, and govern existing resources by generating IaC files for deployed cloud assets.
With Cloud Curate, you can transition unmanaged resources into an IaC-controlled state, ensuring governance and efficiency.
Discovery and inventory
Cloud Curate connects to your cloud accounts and automatically identifies all active resources. It provides a clear inventory, categorized by type, region, and usage, offering a comprehensive view of your cloud ecosystem. This visibility helps teams detect unmanaged or underutilized resources that can be optimized or codified.
Automatic IaC code generation
One of Cloud Curate’s standout features is its ability to generate IaC files like Terraform configuration files for existing resources. This reverse-engineering capability is invaluable for teams inheriting legacy infrastructure or managing manually provisioned resources. By generating IaC code, Cloud Curate brings these resources into the governance fold.
Governance and policy enforcement
Cloud Curate helps enforce policies across both new and existing resources. Integrating with policy enforcement tools makes certain that all cloud assets comply with security, cost, and regulatory requirements. Cloud Curate flags and remediates violations, mitigating the risks of configuration errors and security vulnerabilities.
Cost optimization and resource tracking
Cloud Curate provides insights into cloud resource costs, enabling teams to identify inefficiencies and optimize expenses. It highlights unused or underutilized resources, suggesting cost-saving opportunities while ensuring operational requirements are met.
Integration with Torque
When paired with Torque, Cloud Curate creates a unified IaC management platform. While Cloud Curate focuses on discovery and codification, Torque handles provisioning, orchestration, and policy enforcement. By combining their strengths, they deliver a comprehensive solution for managing every phase of the IaC lifecycle.
Conclusion
Infrastructure as code revolutionizes how we manage and provision infrastructure, offering advantages like automation, consistency, and scalability. By treating infrastructure configurations as code, we can version, share, and reuse setups, leading to more efficient and reliable operations.
Quali Torque and Cloud Curate enhance infrastructure as code benefits by simplifying provisioning, enforcing governance, and providing visibility into resource usage and costs. They make IaC more accessible and manageable for large-scale projects, addressing common challenges software development teams are facing today.
Ready to transform your infrastructure management? See how Quali’s solutions can empower your team and streamline your infrastructure operations today.
