Reusability is a foundational principle in efficient cloud infrastructure operations.
For years, our users have leveraged our Torque platform to discover and leverage the Infrastructure as Code (IaC) resources in their repositories to create reusable Environment as Code blueprints, which can be used to deploy environments automatically.
This has proven valuable for teams with extensive repositories of IaC modules to deliver environments quickly and easily. Some teams previously spent weeks orchestrating non-production environments every time they were needed, then used the Environment as Code approach to turn it into a one-click, self-service method to deploy those environments in just minutes.
However, for teams with limited IaC resources, this approach may have been more difficult. Even for those with the skills to create IaC, the process of creating new IaC modules is an obstacle.
This article will show how Quali Torque’s new Cloud Curate capability bridges this gap by:
- Connecting to the user’s public cloud accounts
- Discovering and displaying the resource configurations deployed via those accounts
- Enabling users to automatically convert those configurations into open-source Terraform files that they can download and leverage
- Leveraging Torque to simplify the provisioning and maintenance of environments leveraging those IaC resources
For a brief look at how Cloud Curate works, check out this video:

Step 1. Connect your AWS & Azure accounts to discover resources deployed
Only those with administrator-level permissions in Torque can generate IaC files from cloud accounts in Torque.
In Torque, those with administrator-level permissions can find Curate under the Account Center, accessible via the drop-down menu to access Spaces.
To connect their cloud accounts, admins only need to provide read permissions for their AWS and Azure accounts. In order to discover resources, Torque only needs access to list resources, read metadata, and access resource details.
Once connected, Torque displays all resources deployed via that account, along with breakdowns to help you understand resource types, location, and status.
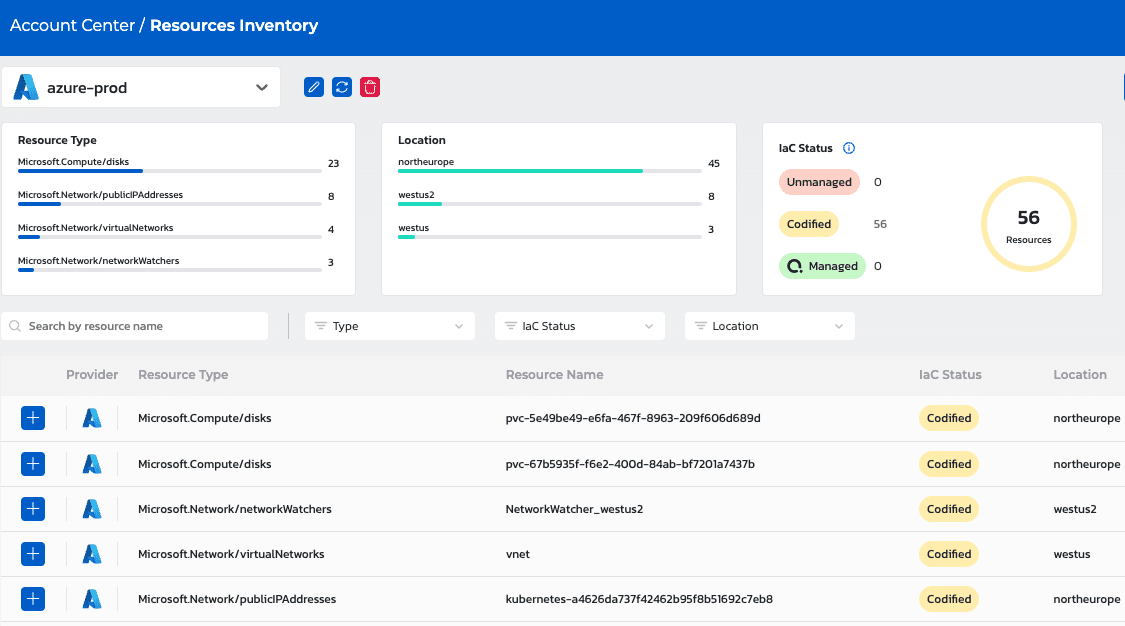
Torque discovers all cloud infrastructure deployed via the user’s AWS and Azure accounts.
Status indicates which resources you’ve already codified as IaC modules using Torque, as well as those which are currently managed via Torque. This helps administrators understand if users are deploying resources outside of the confines of their Torque account, where cloud governance policies and automated Day-2 actions are executed to maintain configurations and security.
Step 2. Select resources and codify as Terraform files
Once you’ve identified resources that you’d like to reuse, you can add them to your Curations.
To convert to Terraform files, select “Curate Collections” to view and initiate the process.
This will allow you to generate and download open-source Terraform files defining the state of each resource configuration you’ve selected.
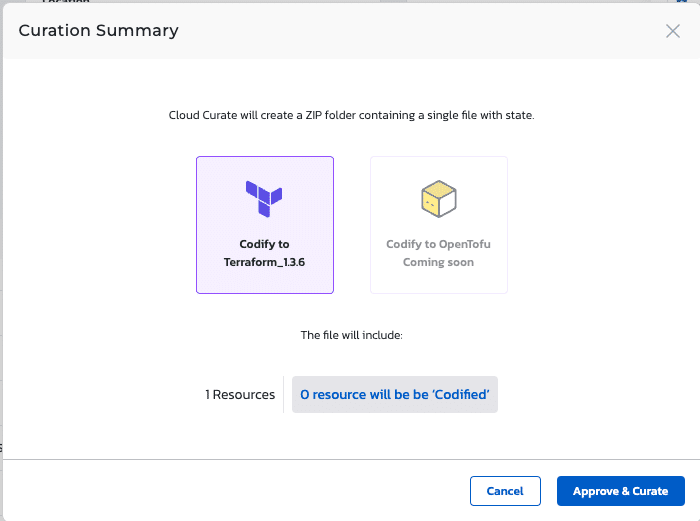
Torque automatically creates Terraform Infrastructure as Code files for the cloud resources discovered via the user’s cloud accounts.
You can now add your new Terraform files to a git repository, which you can then connect to your Torque account to enable simplified provisioning.
Step 3. Enable one-click IaC provisioning via Torque’s self-service catalog
In addition to the ability to generate new IaC modules, Torque also connects to the user’s repositories, discovers the user’s existing IaC modules, and allows them to build and launch environments leveraging the resource configurations in those modules.
Once you’ve connected a repository, you will find all IaC modules on the IaC Assets page in Torque, including the ability to filter by type (e.g. Terraform, OpenTofu, Ansible, etc.), repository (so you can browse through resources across multiple sources), and labels (which can be customized and applied via Torque).
From there you can launch IaC assets directly and also choose to add them to the self-service catalog in Torque. The catalog enables all users to find and launch environments in just a few clicks by enforcing admin-provided default values for inputs and removing the need for security credentials to launch IaC modules. Admins can also customize the names of resources to make them easier to find for users with less expertise in cloud infrastructure, and provide detailed instructions on how to use those resources.
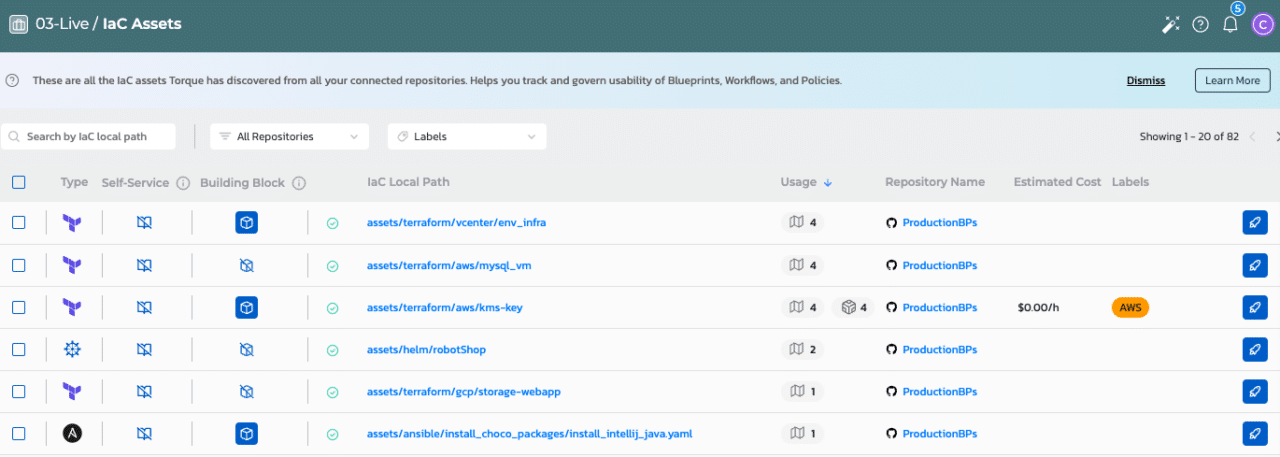
Quali Torque’s IaC assets page allows users to filter through repositories and launch Infrastructure as Code quickly and easily.
Once a user has deployed a resource via the platform, they’re notified that the environment is live and provided a direct link to access the environment outputs.
This approach eliminates the need for ticket requests for infrastructure provisioning by simplifying the process with a governed self-service experience.
Step 4. Use Torque’s Copilot to orchestrate IaC resources into Environment as Code blueprints
One of the most common use cases for Torque is to eliminate the orchestration of environments.
Even for teams with advanced skills and resources defined in IaC, orchestrating environments can be time-consuming and redundant. When environments require multiple cloud resources defined using different tools, engineers typically need to manually code the environment to define the inputs and dependencies to generate the environment outputs. This becomes especially difficult when those IaC resources are defined using different tools, as engineers need to reconcile differences between the tools in order to ensure they will be provisioned successfully.
Torque accelerates this by:
- Normalizing the resource configurations in the platform so they can be easily configured to work together, and
- Using generative AI to orchestrate the resources from the user’s repository, including setting the inputs and defining dependencies, into a reusable Environment as Code blueprint
To accomplish this, administrators can visit the Blueprints page and select, Create New Blueprint. From there, an admin can submit a natural-language AI prompt describing the environment they need and the resources that should be orchestrated to deliver it.
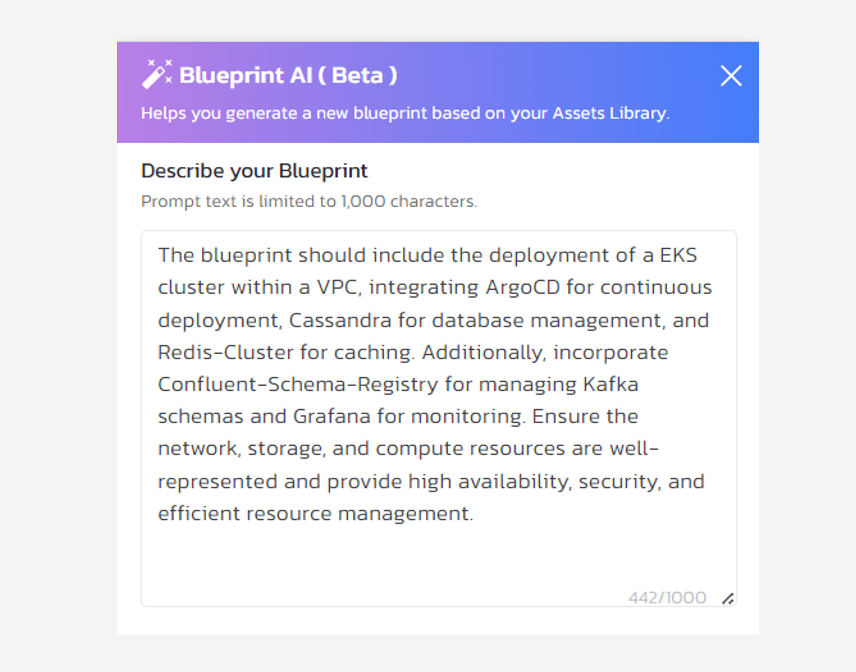
Torque users can submit natural-language AI prompts to automatically orchestrate their Infrastructure as Code resources into environment blueprints.
Leveraging the code for each resource in the user’s library, Torque automatically generates a file with the code to provision the environment and also provides a graphical UI where users can see how the environment is configured.
Once the user is comfortable with the environment’s configuration, they can provision it immediately and add it to the self-service catalog for others to launch it.
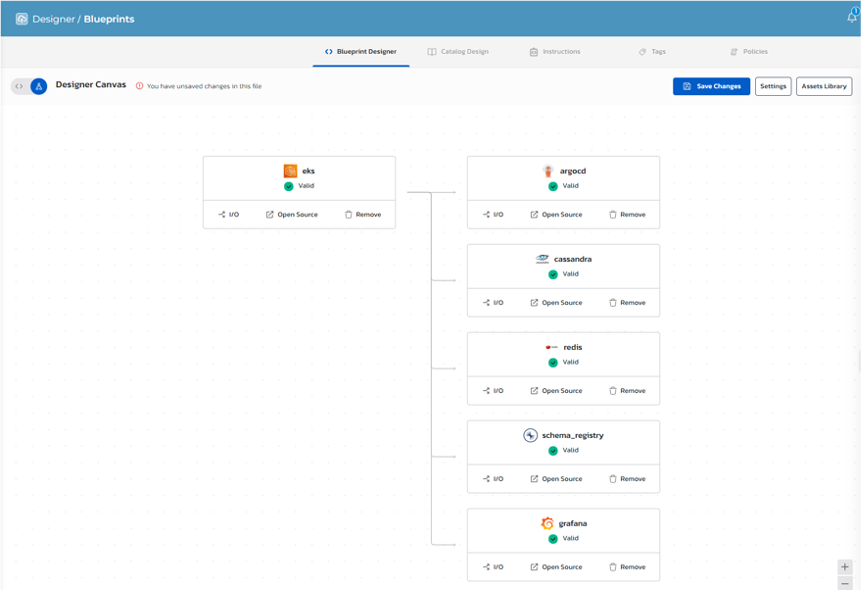
Torque automatically designs that environment and allows users to modify the configuration using the graphical UI.
This further reduces ticket requests while also eliminating redundant orchestration by distributing self-service access for various teams to launch environments based on the blueprint.
Step 5. Track IaC commits to active, inactive, & blueprints for environments
When users need to commit updates to infrastructure code, Torque provides visibility to show how the module defining that code is in use among other users.
From the IaC Assets Page, users can select any IaC module to see Impact Mapping, which provides an overview of all environments and blueprints where that code is in use. This includes the ability to differentiate between active environments and inactive environments, to provide context indicating whether an update to infrastructure code may disrupt ongoing workflows.
Users can also filter by commit to understand how various updates to the IaC module may have impact on the environments in use among their teams.
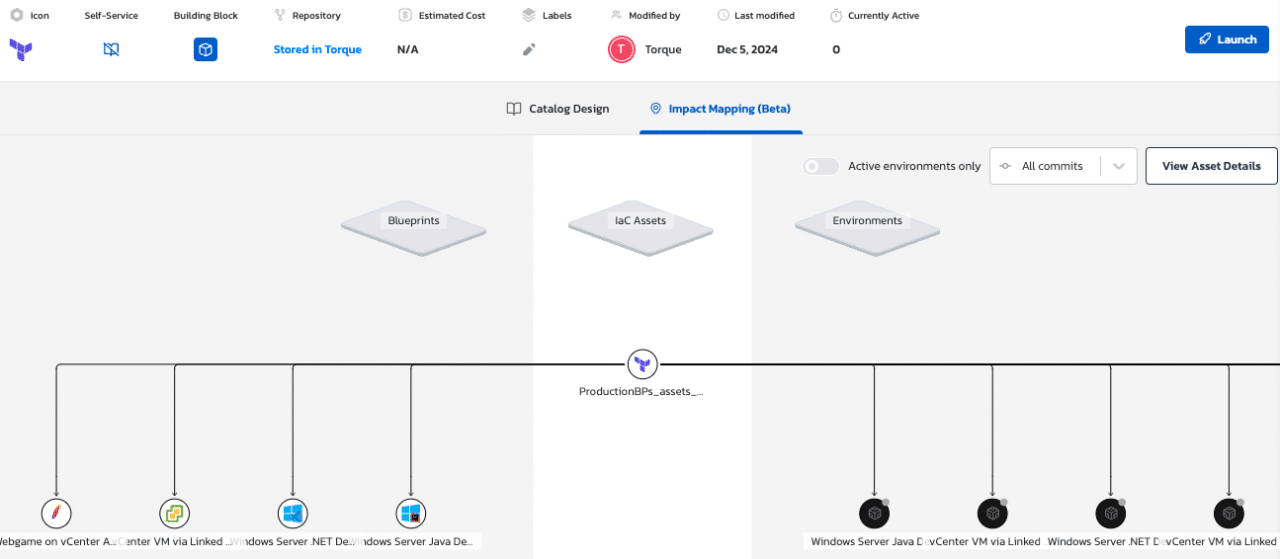
Torque maps any IaC module to the environments that depend on it, so users can collaborate to prevent disruptions to live environments.
This approach helps to streamline Day-2 operations by providing the visibility to understand how updates to infrastructure code may affect their teams.

